
The Emergency POS solution you need to ensure business continuity
The purpose of an emergency solution is to ensure business continuity, so if a security breach happens, nothing happens. You can keep operating as usual, accommodating the biggest C-level worry nowadays: Cyber threats.

Cyber attacks and ransomware
Issues as serious as ransomware and other cyber threats can have crucial consequences for your business, which becomes increasingly evident to every business owner. In recent years, we’ve seen security breaches happen even for big, well-resourced companies, forcing them to close their business for days, resulting in immense revenue loss.
A large number of CEOs rank cyber threats as the biggest threat to their business, and a total of 52 % of CIOs rank cyber security as their top priority! Do you have an emergency solution prepared for a possible cyber attack?
Introducing the Emergency POS solution: How does it work?
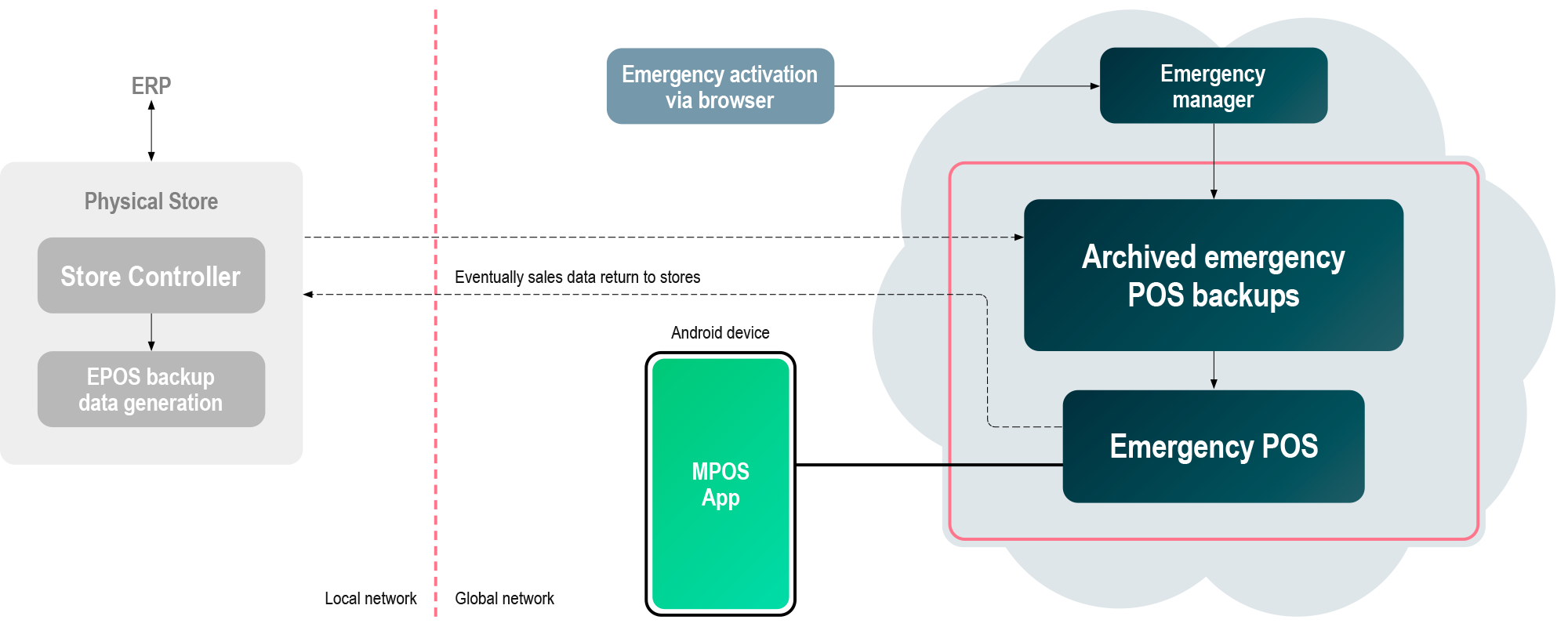
If you experience cyber threats in your POS system, you can switch to use your Emergency mobile POS devices that run on a separate and isolated system. Isolating your Emergency POS from your daily operations prevents a cyber attack on your standard POS from affecting your Emergency POS. Your Emergency POS will be safe and available, enabling you to sell with current prices, when your POS system is under attack.
An Emergency Mobile POS device works just like our ordinary MPOS solution, so your sales personel will be familiar with it. It runs on a secured cloud environment with extremely high uptimes and is extremely secure, and the same goes for the connection between your Emergency POS device and the Emergency POS cloud service. If you simply put a SIM card in your Emergency Mobile POS devices and use a 4G or 5G connection, you can expect extremely high uptimes and very high security for your critical POS infrastructure to handle critical POS emergencies you may experience.
Benefits of an Emergency POS solution

Continue store operations
With an Emergency POS system, you can keep operating your business even in complete technical breakdowns as in ransomware attacks.

Fully stand alone
The Emergency POS system is completely separated from daily operations and thus daily risks.

Prevent revenue loss
When neighboring stores lose revenue because of technical breakdowns that prevent them from selling, you can continue business with your Emergency Mobile POS devices.

Reduce the risk of negative publicity
Keeping your business running in a crisis will increase customer satisfaction and reduce the risk of negative publicity. Additionally, it will reduce employee stress in an emergency.
Do you want to learn more about the Emergency POS solution?

Emergency POS
